Understanding Azure AD in today’s cloud centric world
On 3 minutes
3 minutes
In the past few years, the work/life paradigm has been blurred. There is no longer the work and home separation. We now wake up to our phones or tablets, check our emails, buy stuff online, check Facebook etc.
Our expectation now is that, we should be able to access all these different services from any device that we have, and we do have many. At a minimum, most people will have about 2 devices. We want to be able to access our email on our laptop as well as on the phone.
All these challenge, boils down to identity. I might have 10 different usernames and passwords. How do I remember all these usernames and passwords?
Authentication in the public cloud
Communication over public cloud is commonly done using HTTP and HTTPS (HTTPS preferred because it is encrypted). The authentication commonly used are:
- OAuth
- OAuth 2 (used by Azure AD)
- SAML -used for authentication usually between and identity provider and a service provider
Whenever possible, we want to use MFA where possible.
Azure Active Directory Service
Azure AD is a flat structure allowing users and groups to be created. This contrasts with Active Directory Domain Services which is hierarchical with organizational units that can be nested. There is no Kerberos, because it is not a good fit for an internet-based service. So Azure AD is not AD in the cloud. There is an Azure AD Domain Services that enable limited machine membership and policy application for Azure services.
Authentication is accomplished through protocols such as SAML, WS-Federation and OAuth.
Azure AD as a Federation Broker
Azure AD can be considered as a Federation Broker. It creates a relationship between your on-premises AD and Azure AD instance. From there, Azure AD is federated with all the Microsoft Apps and other Non-Microsoft Apps. This provide single-sign on capabilities and a central point for identity management.
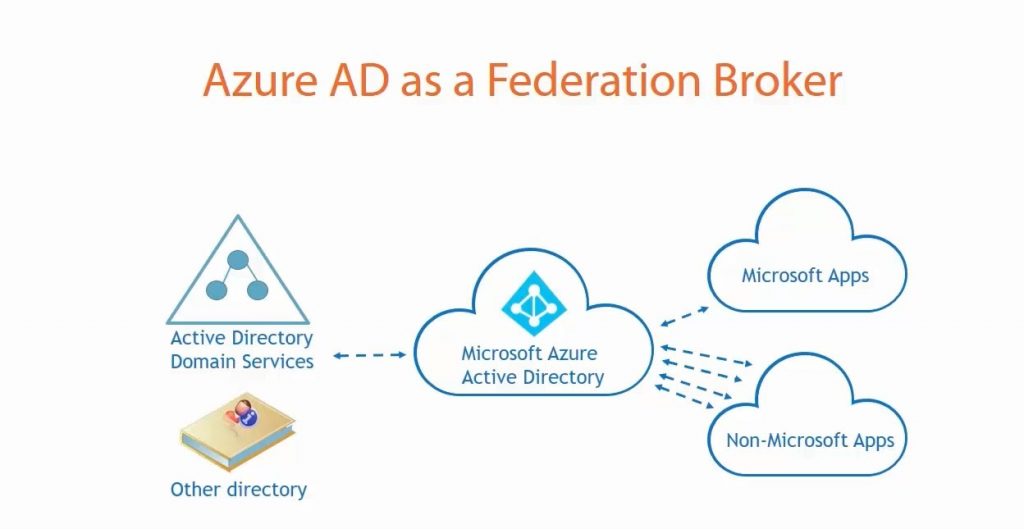
Some of these apps may not have protocol to create objects on their local side, but there is some kind of integration to allow for single-sign on capabilities. Some use credential stuffing, that is Azure AD stores the credentials of that remote service. Example is Twitter.
Azure AD comes in 3 basic types, FREE, BASIC and PREMIUM. The differences come in the number of objects that can be created, the number of single-sign to SASS/Custom Apps/Application Proxy apps, group-based access management/provisioning features, self-service password reset, MFA and others.
References
