Azure Security
On 8 minutes
8 minutes
Protecting your infrastructure and data when you work in the cloud cannot be over emphasized. Every system, architecture, and application need to be designed with security in mind.
It should be stressed that when you are using IaaS, it is your responsibility to patch and secure your operating systems and software, as well as configure your network to be secure.
Moving to platform as a service (PaaS) outsources a lot of security concerns. At this level, Azure is taking care of the operating system and of most foundational software like database management systems.
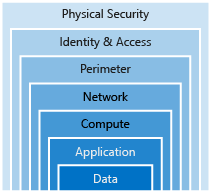
One of the best strategy for securing your services is defence in depth. It provides layers of security. Each layer provides protection so that if one layer is breached, a subsequent layer is already in place to prevent further exposure.
Data
It’s the responsibility of those storing and controlling access to data to ensure that it’s properly secured:
- Stored in a database
- Stored on disk inside virtual machines
- Stored on a SaaS application such as Office 365
- Stored in cloud storage
Application
- Ensure applications are secure and free of vulnerabilities.
- Store sensitive application secrets in a secure storage medium.
- Make security a design requirement for all application development.
Compute
- Secure access to virtual machines.
- Implement endpoint protection and keep systems patched and current.
Networking
- Limit communication between resources.
- Deny by default.
- Restrict inbound internet access and limit outbound, where appropriate.
- Implement secure connectivity to on-premises networks.
Perimeter
- Use distributed denial of service (DDoS) protection to filter large-scale attacks before they can cause a denial of service for end users.
- Use perimeter firewalls to identify and alert on malicious attacks against your network.
Identity and access
- Control access to infrastructure and change control.
- Use single sign-on and multi-factor authentication.
- Audit events and changes.
Physical security
- Physical building security and controlling access to computing hardware within the data center is the first line of defence.
Identity and access
With the explosion of bring your own device (BYOD), mobile apps, and cloud applications, network perimeters, their firewalls, and physical access controls are no longer the best primary way to protect corporate data. Identity has become the new primary security boundary.
Single sign-on
Single sign-on is a great identity security feature you should use. Users need to remember only one ID and one password. Access across applications is granted to a single identity tied to a user, thereby simplifying the security model.
Azure Active Directory (AD) has built in support for synchronizing with your existing on-premises Active Directory or can be used stand-alone. This means that all your applications, whether on-premises, in the cloud (including Office 365), or even mobile can share the same credentials.
Multi-factor authentication
Multi-factor authentication (MFA) provides additional security for your identities by requiring two or more elements for full authentication
Providing identities to services
It’s usually valuable for services to have identities. Often, and against best practices, credential information is embedded in configuration files. Use service principals and managed identities.
A principal is an identity (a thing that can be authenticated) acting with certain roles or claims. Groups are often also considered principals because they can have rights assigned.
A service principal is an identity that is used by a service or application. And like other identities, it can be assigned roles.
Managed identities for Azure services makes the creation and management of service principal easy. A managed identity can be instantly created for any Azure service that supports it. When you create a managed identity for a service, you are creating an account on the Azure AD tenant. The Azure infrastructure will automatically take care of authenticating the service and managing the account.
More info at:
https://docs.microsoft.com/en-us/azure/active-directory/develop/howto-create-service-principal-portal
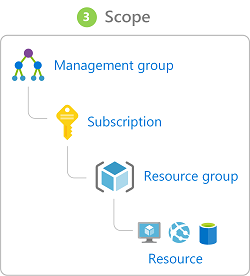
Role-based access control
Use RBAC to map identities to roles. Roles are sets of permissions that users can be granted to access an Azure service instance. Roles can be granted at the individual service instance level, but they also flow down the Azure Resource Manager hierarchy.
Privileged Identity Management
Azure AD Privileged Identity Management (PIM) is an additional, paid-for offering that provides oversight of role assignments, self-service, and just-in-time role activation and Azure AD and Azure resource access reviews.
Encryption
Encryption makes data unreadable and unusable to unauthorized viewers. You can use symmetric or asymmetric encryption.
Symmetric encryption uses the same key to encrypt and decrypt the data.
Asymmetric encryption uses a public key and private key pair. Either key can encrypt but a single key can’t decrypt its own encrypted data. To decrypt, you need the paired key. Transport Layer Security (TLS) (used in HTTPS) is an example.
Encryption is typically approached in two ways: encryption at rest and encryption in transit.
Encryption in Transit
- Encrypt the data at the application layer prior to sending it over a network. HTTPS is an example of application layer in transit encryption.
- Set up a secure channel, like a virtual private network (VPN), at a network layer, to transmit data between two systems.
Encryption at rest
Encryption of data at rest ensures that the stored data is unreadable without the keys and secrets needed to decrypt it.
Encryption on Azure
Azure provides many ways to help you encrypt your data, be it at rest or in transit.
Encrypt raw storage
Azure Storage Service Encryption for data at rest helps you protect your data to meet your organizational security and compliance commitments.
Encrypt virtual machines
Storage Service Encryption provides low-level encryption protection for data written to physical disk. Azure Disk Encryption leverages the industry-standard BitLocker feature of Windows and the dm-crypt feature of Linux to provide volume encryption for the OS and data disks. The solution is integrated with Azure Key Vault to help you control and manage the disk encryption keys and secrets (and you can use managed service identities for accessing Key Vault).
Encrypt databases
Transparent data encryption (TDE) helps protect Azure SQL Database and Azure Data Warehouse against the threat of malicious activity. It performs real-time encryption and decryption of the database, associated backups, and transaction log files at rest without requiring changes to the application. By default, TDE is enabled for all newly deployed Azure SQL Database instances.
Encrypt secrets
How do we ensure that the keys use to encrypt and decrypt data are themselves secure? Azure Key Vault is a cloud service that works as a secure secrets store. Key Vault allows you to create multiple secure containers, called vaults. These vaults are backed by hardware security modules (HSMs). Vaults help reduce the chances of accidental loss of security information by centralizing the storage of application secrets.
Because Azure AD identities can be granted access to use Azure Key Vault secrets, applications with managed service identities enabled can automatically and seamlessly acquire the secrets they need.
Protecting your network
Azure provides the tools for a layered approach to securing your network footprint.
Internet protection
To provide inbound protection at the perimeter, you have a couple of choices:
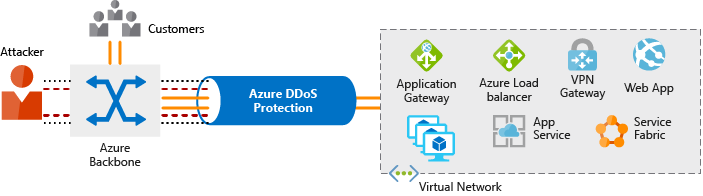
- Azure Application Gateway is a load balancer that includes a web application firewall that provides protection from common, known vulnerabilities.
- Network virtual appliances (NVAs) are ideal options for non-HTTP services or advanced configurations, and are similar to hardware firewall appliances.
Azure DDoS protection provides basic protection across all Azure services and enhanced protection for further customization for your resources. Azure DDoS protection blocks attack traffic and forwards the remaining traffic to its intended destination. Within a few minutes of attack detection, you are notified using Azure Monitor metrics.
Virtual network security
Once inside a virtual network (VNet), it’s crucial that you limit communication between resources to only what is required.
For communication between virtual machines, network security groups are a critical piece to restrict unnecessary communication. They provide a list of allowed and denied communication to and from network interfaces and subnets, and are fully customizable.
Network integration
It’s common to have existing network infrastructure that needs to be integrated to provide communication between on-premises networks and services in Azure. Use Virtual private network (VPN) connections or Azure ExpressRoute.
Disclosure
This a a summarized version of the azure security documentation from Microsoft. You can access the whole content from https://docs.microsoft.com/en-us/learn/modules/intro-to-security-in-azure/1-introduction